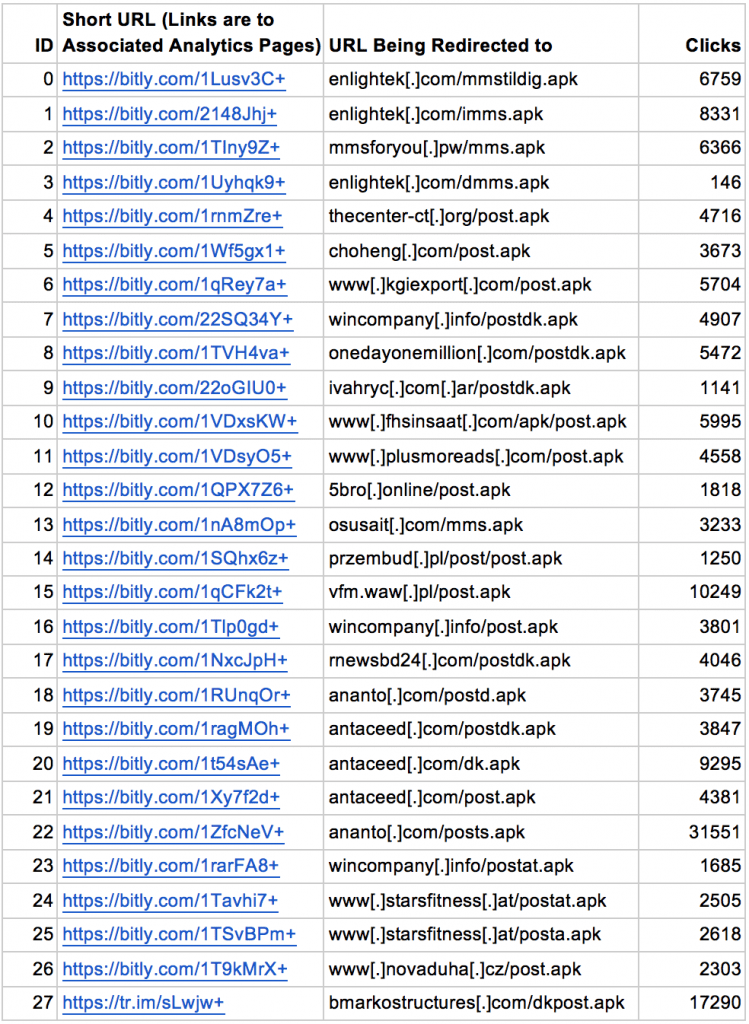
The malicious actions were very similar to RuMMS campaign which was aimed at the Russian segment. Unlike RuMMS, described in 3 campaigns which were using the user’s screen spoofing technique. Attackers display the fake user interface of the application instead of the bank and intercepted credentials for accessing online banking. Attackers initially organize the work of C & C servers and sites that to distribute malware, and then send out the victims of SMS messages containing a link to the malicious software. After contact with the system Trojan scans the victim’s device, and monitors the applications running in the background. Once the user launches the application for working with online banking, the malware displays the interface on top of a running application. Thus the user is prompted for credentials in the form, controlled by the hackers. The malware is aimed at a number of specific applications and activates the overlay only after starting the last task. However, malicious activity is not stopped in May. From February to June 2016, researchers found more than 55 modifications of malware propagating across the Europe: Denmark, Italy, Germany, Austria, etc. Unlike RuMMS, the current campaign is not only using the free hosting to host malware. As the attackers register domain names, use a shortened Bit.ly link service and compromised websites. In June, in addition to the arsenal of Bit.ly intruders appeared, such as the URL shortening service tr.im, jar.mar and is.gd. FireEye Security Experts found 12 C & C servers hosted in 5 countries. The server with the IP-address “85.93.5.109 24” containing malicious applications which were used in two campaigns, “85.93.5.139” used in 8 applications. In addition, the 4 C & C servers are located on a subnet “85.93.5.0/24”. This indicates the presence of control over the network resources on the network segment. As we all know that the URL shortening services usually provide link analytics services, which allows us to collect data on how many users from which countries clicked the particular short links and when it happened. Hence, using these services, the security company FireEye found there have been at least 161,349 clicks on the 30 short links redirecting to the overlay malware and each of which can drive to the infection of one Android device.